
A rotary-wing aircraft is a type of aircraft that uses rotary wings, commonly known as rotors, to generate lift and propulsion. Unlike fixed-wing aircraft, which rely on the forward motion of the aircraft to create lift with stationary wings, rotary-wing aircraft achieve lift and thrust through the rotation of one or more rotor systems. Rotary-wing aircraft used for a variety of missions including transport, reconnaissance, and attack.

Satellite Communication refers to the use of artificial satellites to transmit and receive signals for data, voice, and video communication over long distances. It enables global connectivity, especially in remote or inaccessible areas, by relaying signals between ground stations and users.

An air defense system is a military structure designed to detect, track, intercept, and neutralize incoming airborne threats, such as enemy aircraft, missiles, or drones. These systems use a combination of radar, sensors, anti-aircraft missiles, and fighter jets to protect a designated airspace or territory.

An Unmanned Aerial Vehicle (UAV) is an aircraft that operates without an onboard pilot, either by remote control or through autonomous systems. UAVs are used in various fields such as military, disaster relief, logistics, and environmental monitoring, offering high maneuverability and the ability to avoid risks.

An Information System (IS) is a structured system that collects, processes, stores, and distributes information to support decision-making, coordination, control, analysis, and visualization within an organization. It integrates people, processes, hardware, software, and data to achieve business or operational goals. 💡 Common Types of Information Systems ✔️Management Information Systems (MIS) ✔️Enterprise Resource Planning (ERP) ✔️Customer Relationship Management (CRM) ✔️Decision Support Systems (DSS) ✔️Transaction Processing Systems (TPS)

Combat Vehicles: Vehicles designed for direct engagement in battle, equipped with weaponry and armor, such as tanks and infantry fighting vehicles. Support Vehicles: Vehicles used to provide logistical, medical, or operational support to combat forces, such as transport trucks, ambulances, and supply carriers.

An Eavesdropping Detection System is a security solution designed to detect unauthorized listening devices or interception of communications. It monitors various frequencies and signals, such as radio waves, Wi-Fi, Bluetooth, and other wireless communication channels, to identify potential eavesdropping equipment or hacking attempts. The system helps safeguard sensitive information and protect privacy in environments like government buildings, corporate offices, and personal spaces.

Radar and sensors are devices that use radio waves, sound waves, or other signals to detect the location, speed, and size of objects, as well as to gather environmental information. They play a crucial role in fields like military, aviation, and meteorology by enabling real-time monitoring and data provision.

A Special Vehicle refers to a vehicle designed and manufactured for a specific purpose beyond general transportation. These vehicles are often equipped with specialized equipment, modifications, and technology to perform unique tasks in various industries, including military, emergency response, construction, and exploration.

Artificial Intelligence (AI) in the military refers to the use of advanced algorithms, machine learning, and autonomous systems to enhance defense operations, decision-making, and combat effectiveness. Military AI applications include autonomous drones, robotic combat systems, intelligence analysis, cybersecurity, electronic warfare, and battlefield decision support. AI improves target recognition, threat detection, logistics management, and mission planning by processing vast amounts of data in real time. It also powers autonomous and semi-autonomous weapons systems, such as loitering munitions, unmanned ground vehicles (UGVs), and AI-driven surveillance systems, increasing operational efficiency and reducing human risk in high-threat environments.

An Anti-Drone System is an integrated technology designed to detect, identify, track, and neutralize unmanned aerial vehicles (UAVs) or drones that pose potential threats to safety, security, or privacy. These systems are essential for safeguarding critical infrastructure, military installations, public events, and other sensitive areas from unauthorized or malicious drone activities.

An Endpoint Security Solution is a comprehensive security system designed to protect individual devices (endpoints) such as desktops, laptops, and servers from a variety of cyber threats. It provides real-time monitoring, detection, response, and reporting to secure endpoints within an organization’s network.

Missile Systems: Integrated systems designed to launch and guide missiles toward a designated target. These systems typically include launch platforms, guidance systems, and supporting equipment for target acquisition and tracking, and are used for offensive or defensive military operations.

Network Security Equipment refers to specialized hardware devices designed to protect computer networks from unauthorized access, cyberattacks, data breaches, and other security threats. These devices act as the first line of defense in securing digital infrastructure by monitoring, filtering, and controlling incoming and outgoing network traffic based on pre-established security rules. 💡 Common Types of Network Security Equipment ✔️Firewall: Blocks unauthorized access while permitting legitimate communication. Intrusion Detection/Prevention Systems (IDS/IPS): Monitors network traffic for suspicious activity and takes action against potential threats. ✔️Unified Threat Management (UTM): An all-in-one device combining firewall, antivirus, content filtering, and intrusion prevention. ✔️VPN Gateway: Secures remote access by encrypting connections over public networks. ✔️Web/Application Gateways: Filters traffic at the application level to prevent attacks like SQL injection or XSS. ✔️Network Access Control (NAC): Controls which devices are allowed to connect to the network based on security policies.

Small arms are portable, individual or crew-served firearms designed for personal use in military, law enforcement, or civilian applications. They typically include handguns (pistols, revolvers), rifles, carbines, submachine guns, shotguns, and light machine guns. ✅ Key Characteristics of Small Arms: Man-portable: Can be carried and operated by an individual or a small team. Caliber: Usually below 20mm (e.g., 5.56mm, 7.62mm, 9mm, .50 caliber). Uses: Infantry combat, self-defense, law enforcement, and sport shooting. Small arms are distinct from heavy weapons, which require vehicles, crews, or mounting systems for operation, such as heavy machine guns, mortars, and artillery.

A space-based system refers to a system that utilizes satellites or devices operating in space to monitor, communicate, explore, and collect data about the Earth and the surrounding environment. These systems are employed to enhance the efficiency of Earth observation, environmental monitoring, defense, and communication networks.

A fixed-wing aircraft is an aircraft with wings that do not move in relation to the main body of the aircraft. The aircraft generates lift through its wings as it moves forward, typically using an engine for propulsion. Common examples include airplanes and gliders, and they are widely used for commercial, military, and recreational purposes.

C4ISR stands for Command, Control, Communications, Computers, Intelligence, Surveillance, and Reconnaissance. It represents an integrated system designed to enhance a military's operational awareness and decision-making. This system collects, processes, and shares critical data to coordinate and monitor battlefield operations effectively.
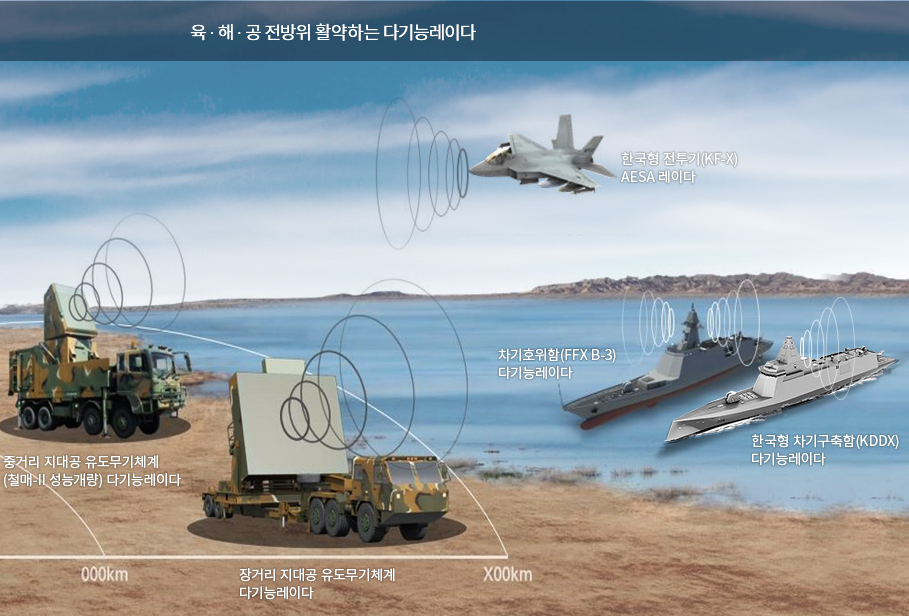
A multi-function radar (MFR) is an advanced radar system capable of performing multiple tasks simultaneously, such as detecting, tracking, and guiding weapons toward various targets, including aircraft, missiles, and other threats. MFR systems are designed for flexibility and efficiency, often combining surveillance, targeting, and engagement functions in one unit.

A server platform is the foundational hardware and software environment designed to host, manage, and deliver computing resources and services. It includes the physical server hardware (such as CPUs, memory, storage, and networking components) as well as the firmware, operating systems, and management tools that enable efficient, secure, and scalable operation. Server platforms are built to support critical workloads in enterprise IT environments, including applications, databases, virtualization, cloud services, and high-performance computing. They are optimized for performance, reliability, security, and manageability, forming the backbone of modern data centers and cloud infrastructures.

A Weapon Control System (WCS) is an advanced integrated system designed to manage and control various weapon platforms, enabling precise target acquisition, tracking, and engagement in diverse operational environments. WCS is utilized across land, naval, and air forces, enhancing the effectiveness and accuracy of modern combat systems.

A Cybersecurity Platform serves as a unified defense system that helps organizations detect, respond to, and prevent a wide range of cyber threats, while also supporting regulatory compliance and business continuity in an increasingly digital world. 💡 Key Features of a Cybersecurity Platform ✔️Threat Detection and Prevention: Uses AI, machine learning, or signature-based tools to identify and block malicious activity. ✔️Endpoint Security: Protects user devices (PCs, mobiles, servers) connected to the network. ✔️Network Security: Monitors and filters traffic to prevent intrusions, DDoS attacks, or data leaks. ✔️Cloud Security: Safeguards cloud-based resources and workloads. ✔️Security Information and Event Management (SIEM): Aggregates and analyzes logs for real-time threat monitoring and incident response. ✔️Identity and Access Management (IAM): Ensures that only authorized users can access specific systems or data.